Apologies for the late reply.
@Avron I tried sudo journalctl -f and also looked at it via Logs on the Cockpit terminal and it honestly didn’t really pop up something that seems worthwhile besides that it wasnt popping up any ssh-keygen suggestions.
FREEDOMBOX:443 192.168.50.1 - - [17/Jan/2024:00:23:40 +0800] "GET /plinth/sys/backups/repositories/add-remote/ HTTP/2.0" 200 4465 "https://FREEDOMBOX/plinth/sys/backups/repositories/add-remote/" "Mozilla/5.0 (X11; Linux x86_64; rv:121.0) Gecko/20100101 Firefox/121.0"
FREEDOMBOX:443 192.168.50.1 - - [17/Jan/2024:00:23:38 +0800] "GET /plinth/sys/backups/repositories/9a93a4fc-b48b-11ee-b0ca-dca632cd0329/ssh-verify/ HTTP/2.0" 302 0 "https://FREEDOMBOX/plinth/sys/backups/repositories/add-remote/" "Mozilla/5.0 (X11; Linux x86_64; rv:121.0) Gecko/20100101 Firefox/121.0"
pam_unix(sudo:session): session closed for user root
pam_unix(sudo:session): session opened for user root(uid=0) by (uid=110)
plinth : PWD=/ ; USER=root ; COMMAND=/usr/share/plinth/actions/actions backups is_mounted --write-fd 18
# backups..is_mounted(…)
/usr/bin/plinth
Connected (version 2.0, client OpenSSH_8.9p1)
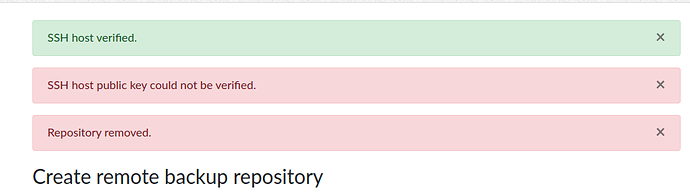
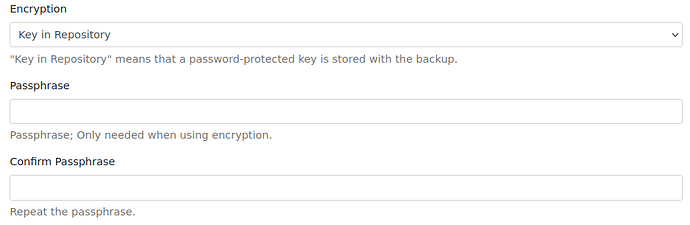
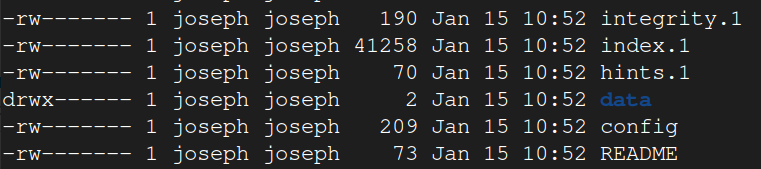
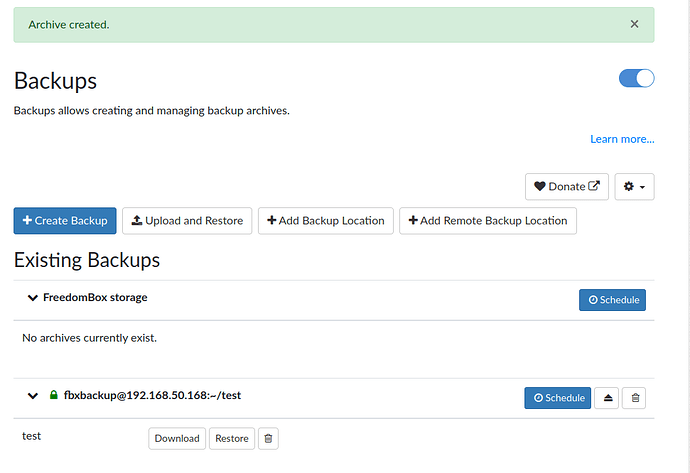
@joseph Many thanks joseph for your elaborate answer, it was very clear with its intentions and easy to follow. I have to say that I’ve successfully made a connection and a backup with your answer as can be seen on the screenshot below (Although on a temporary test directory). I have to mention that for some reason doing PCNAME.local doesn’t really work for me (spouts out getaddrinfo errors and seems like it cant resolve it), and it only works if I address it via its IP.
Also I was trying to mount the backup location with a mounted external HDD on my PC which resides on /media/USER/HDDNAME but it threw me an [Errno 13] Permission Denied error. I’m trying to figure out a way to do this. Full Error log below as I can’t make another screenshot as a new user.
(EDIT) I’ve successfully mounted my external HDD as a backup location. The problem was that it was mounting using my current user, which I did not intend as I made a different user (fbxbackup) with its own ssh keys, and authenticated the entire process with that user in mind. The permission denied error was genuinely saying the permissions were denied.
The fix I did for this was to login to the other user and took ownership of the external hard drive via the Disks app on GNOME.
Now it’s accurately showing up as /media/USER/Backup, and has mounted successfully.
(EDIT 2) That wasn’t a permanent change, a permanent change is changing the mount options of the drive (also using the Disks app) and making sure it’s mounted at the correct intended directory, mine is /media/USER/Backup. I think this is doable manually by fstab as the changes are applied there anyway, but doing it myself just crashed my PC, lol.
/usr/bin/plinth
Error adding repository: [Errno 13] Permission denied
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/plinth/modules/backups/views.py", line 425, in _save_repository
repository.initialize()
File "/usr/lib/python3/dist-packages/plinth/modules/backups/repository.py", line 430, in initialize
self._ensure_remote_directory()
File "/usr/lib/python3/dist-packages/plinth/modules/backups/repository.py", line 498, in _ensure_remote_directory
sftp_client.listdir(dir_path)
File "/usr/lib/python3/dist-packages/paramiko/sftp_client.py", line 218, in listdir
return [f.filename for f in self.listdir_attr(path)]
^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/paramiko/sftp_client.py", line 239, in listdir_attr
t, msg = self._request(CMD_OPENDIR, path)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/paramiko/sftp_client.py", line 822, in _request
return self._read_response(num)
^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/paramiko/sftp_client.py", line 874, in _read_response
self._convert_status(msg)
File "/usr/lib/python3/dist-packages/paramiko/sftp_client.py", line 905, in _convert_status
raise IOError(errno.EACCES, text)
PermissionError: [Errno 13] Permission denied
In hindsight while following the instructions, I guess the only steps that I’ve forgotten to do were to tell the users to trust the users (authorized_keys). I assume that’s the missing part, although I would assume freedombox should’ve done it automatically when it asked me to verify the shown public key. I find this behavior strange if it’s not achievable via the web and have to do this manually through console.
Thank you for the recommendations and practices for protection, before doing all this I made sure to make a separate user (fbxbackup) so that I’m certain my backups is only accessed by a user made for one purpose. Also I’ve ensured that it is encrypted. The only reason why I’m doing all this is because my Raspberry Pi couldn’t handle 2 hard drives so I opted to backup my freedombox through my PC instead.
Many thanks again for the answer, I really appreciated it.