I am able to connect to my OpenVPN service, but no data flows once the connection is made. I tried what is mentions in another similar topic, but it did not help.
First,
$ uname -a
Linux freedombox 6.1.0-13-armmp-lpae #1 SMP Debian 6.1.55-1 (2023-09-29) armv7l GNU/Linux
This is a box I bought several years ago (Olimex A20-OLinuXino-LIME2, 2x ARMv7 Processor rev 4 (v7l)). I have reinstalled the image myself about 6 months ago, downloading it from Freedombox site.
I have turned on OpenVpn and done all configuration through the Plinth UI and I was able to generate all the files for server and client. I am using my phone as a client and I am able to connect, but once I connect data does not flow. I cannot connect on the phone to anything.
I have tried several modifications after that, but was not able to get anywhere.
OpenVpn Config
$ cat /etc/openvpn/server/freedombox.conf
port 1194
proto udp
# proto udp6
dev tun0
# client-to-client
ca /etc/openvpn/freedombox-keys/pki/ca.crt
cert /etc/openvpn/freedombox-keys/pki/issued/server.crt
key /etc/openvpn/freedombox-keys/pki/private/server.key
dh none
server 10.91.0.0 255.255.255.0
keepalive 10 120
verb 3
log-append openvpn.log
tls-server
tls-version-min 1.2
cipher AES-256-CBC
script-security 2
In the config above I tried both dev tun0 and dev tun, but neither seemed to work. I also have disabled udp6 on purpose to make things simpler.
tun0 interface config
$ cat /etc/NetworkManager/system-connections/tun0.nmconnection
[connection]
id=tun0
uuid=6aef5d32-b9a2-476a-9e84-c5b93a499c98
type=tun
autoconnect=false
interface-name=tun0
timestamp=1699982689
[tun]
[ipv4]
method=auto
[ipv6]
addr-gen-mode=default
method=disabled
[proxy]
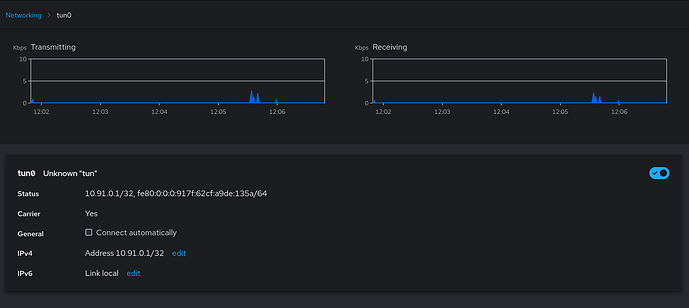
I have explicitly disabled the ipv6 here as well. However, for some reason the Cockpit app is showing different settings and also showing data flowing in both transmitting and receiving directions:
Firewall.
I have removed OpenVpn and tun0 interface from the internal zone:
$ sudo cat /etc/firewalld/zones/external.xml
<?xml version="1.0" encoding="utf-8"?>
<zone>
<short>External</short>
<description>For use on external networks. You do not trust the other computers on networks to not harm your computer. Only selected incoming connections are accepted.</description>
<service name="ssh"/>
<service name="http"/>
<service name="https"/>
<service name="openvpn"/>
<masquerade/>
</zone>
$ sudo cat /etc/firewalld/zones/internal.xml
<?xml version="1.0" encoding="utf-8"?>
<zone>
<short>Internal</short>
<description>For use on internal networks. You mostly trust the other computers on the networks to not harm your computer. Only selected incoming connections are accepted.</description>
<service name="ssh"/>
<service name="mdns"/>
<service name="samba-client"/>
<service name="dhcpv6-client"/>
<service name="http"/>
<service name="https"/>
<service name="dns"/>
<service name="dhcp"/>
<interface name="tun1"/>
<interface name="tun2"/>
<interface name="tun3"/>
<interface name="tun4"/>
<interface name="tun5"/>
<interface name="tun6"/>
<interface name="tun7"/>
</zone>
Any suggestion on where I should look further, what kind of logs I need is greatly appreciated.