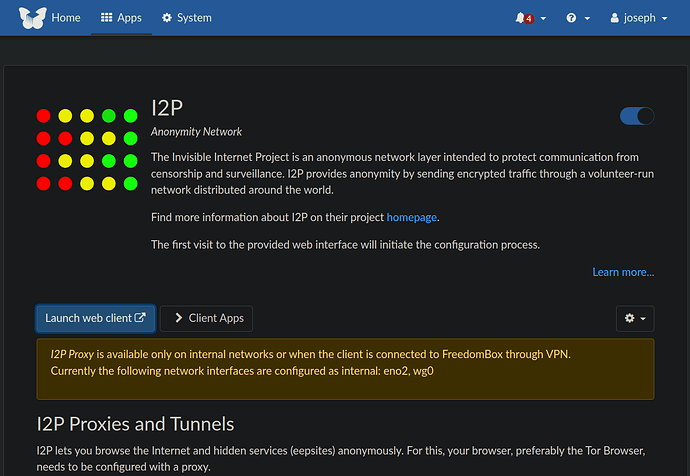
Successful Workaround
Summary
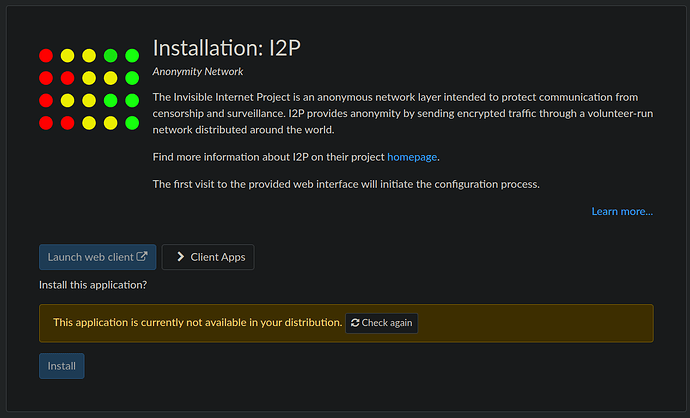
i2p is not currently available in Debian. This package was removed by Debian maintainers because of a security issue which creates risk only to users maintaining eepsites (i2p network web server). Users not maintaining an eepsite are not at risk of the attack method listed earlier in this thread.
A skilled Debian user can get i2p running again on their Freedombox with these instructions. This workaround does require root privilege and modification of the system from a terminal. It’s not for everybody, but it appears to be working for me.
Risk Disclosure
We are connecting apt to a new package repository. When you examine the apt changes you will see that these appear to be limited to i2p, so I do not expect Freedombox to add an unexpected package from this location.
Procedure
Reference i2p installation instruction from geti2p.net. Do not follow these instructions - they didn’t work for me.
Reference i2p workaround installation from i2p forum. We will use this one with modifications.
We will be using packages from the Ubuntu PPA Focal repository. We will:
- Get and check the repository key
- Add the key to the system keyring (we deviate from the published workaround here)
- Add the Ubuntu PPA repository to apt
- Install i2p from plinth like you normally would
Repository Key Download
We will not follow the published workaround for this step. If you do, it will work, but you will see apt complain about using the deprecated apt-key command. I took the opportunity to figure out the new way to manage repository keys.
Published Download Command
curl 'https://keyserver.ubuntu.com/pks/lookup?op=get&search=0x474bc46576fae76e97c1a1a1ab9660b9eb2cc88b ' | sudo apt-key add -
You should copy and paste this command from the i2pforum page as discuss.freedombox.org will tamper with the quotes. If you do this it will work fine, but apt will complain about your having used the deprecated apt-key command.
New Key Download
We’ll only use the first bit of the published key download to get the public key without adding it to the apt repository. Copy and paste the command from the workaround page but delete the last part:
curl 'https://keyserver.ubuntu.com/pks/lookup?op=get&search=0x474bc46576fae76e97c1a1a1ab9660b9eb2cc88b’ | sudo apt-key add -
Next redirect the curl output to a file - your command will look like this:
$curl 'https://keyserver.ubuntu.com/pks/lookup?op=get&search=0x474bc46576fae76e97c1a1a1ab9660b9eb2cc88b ' > i2p-archive-ppa-focal-keyring
Be sure to remove the space between the end of the hexidecimal string and the single quote (discuss.freedombox.org changes quotes to make your post look pretty, but the syntax will be wrong for copy/paste into the command line.)
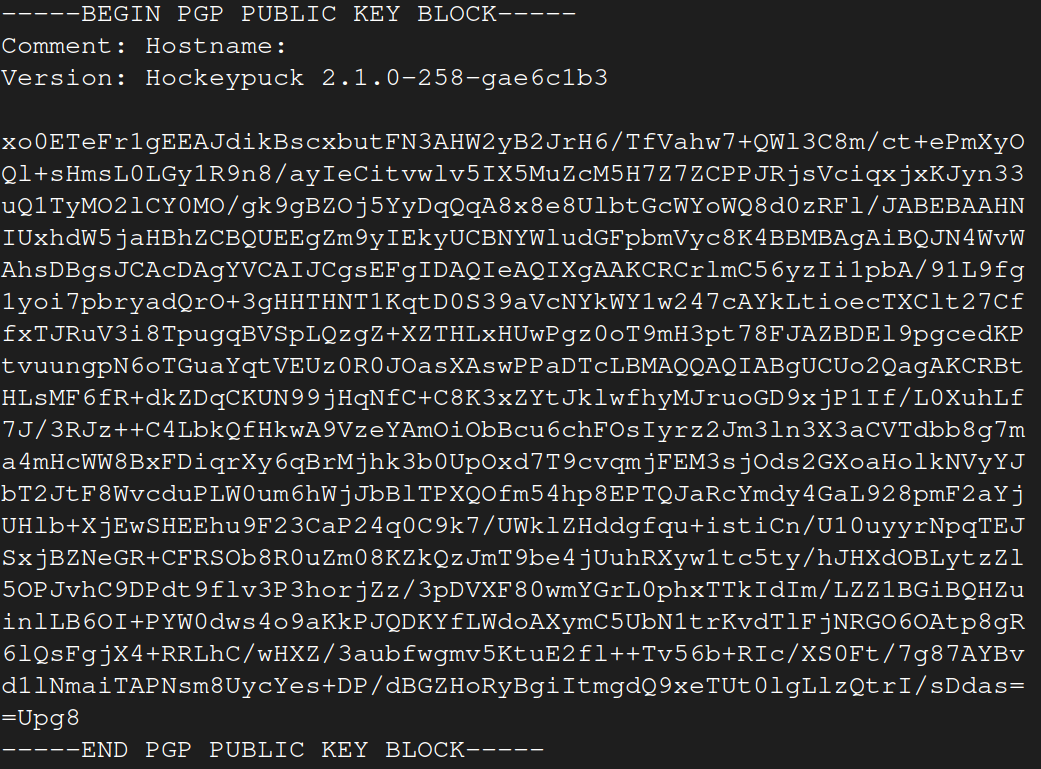
You now have a file named i2p-archive-ppa-focal-keyring in your working directory which has these contents:
Next change this file into gpg format - again you do not need to be root yet.
$gpg --dearmor i2p-archive-ppa-focal-keyring
This will create the file i2p-archive-ppa-focal-keyring.gpg
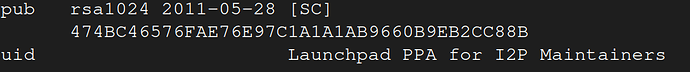
Normally at this point best practice is to compare the key fingerprint with a published key fingerprint to be certain you are connecting to the repository to which you think you are connecting.
$gpg --show-keys i2p-archive-ppa-focal-keyring.gpg
You should check the key fingerprint from the GPG file against the key published by the PPA repository maintainer. I skip this step because I couldn’t find this easily. If you do this - please share your results especially if the keys don’t check out.
$gpg --show-keys i2p-archive-ppa-focal-keyring.gpg
Now we copy the .gpg key into /usr/share/keyrings (as root):
sudo cp i2p-archive-ppa-focal-keyring.gpg /usr/share/keyrings
At this point we have the encryption key for the Ubuntu PPA Focal repository configured. Next we set up apt.
Set up apt i2p repository using PPA
Create a new apt source for i2p in /etc/apt/sources.list.d named i2p.list.
$sudo nano /etc/apt/source.list.d/i2p.list with these contents:
deb [signed-by=/usr/share/keyrings/i2p-archive-ppa-focal-keyring.gpg] Index of /i2p-maintainers/i2p/ubuntu focal main
deb-src [signed-by=/usr/share/keyrings/i2p-archive-ppa-focal-keyring.gpg] Index of /i2p-maintainers/i2p/ubuntu focal main
Check that everything is working with $sudo apt update
Hit:1 tor+http://deb.debian.org/debian bookworm InRelease
Hit:2 tor+http://deb.debian.org/debian bookworm-updates InRelease
Hit:3 Index of /i2p-maintainers/i2p/ubuntu focal InRelease
Hit:4 tor+http://deb.debian.org/debian bookworm-backports InRelease
Hit:5 tor+http://security.debian.org/debian-security bookworm-security InRelease
Reading package lists… Done
Building dependency tree… Done
Reading state information… Done
All packages are up to date.
Hit: 3 Index of /i2p-maintainers/i2p/ubuntu focal InRelease is what we were hoping to see.
Install i2p from plinth like you normally would.