Thanks for the clarification.
UPDATE
I don’t like the idea of the DMZ as it seems to just fully expose the Pi to the internet, which is not really what I want.
I’ve been exploring this a little bit more and hit on a set up using my DD-WRT router - described below. I would really welcome any feedback regarding if my understanding of my set up is correct and comments about the strengths/weaknesses of it, if it does in fact make sense and does add extra protection to my local network machines?
Background
As mentioned above, the reason I want to isolate the Raspberry Pi 3B+ web server is that I had it set up with Freedombox, NextCloud and Wordpress and someone hacked into it and changed the web root’s index.html file. There wasn’t anything sensitive on the Pi, but it did freak me out that it could be a possible way to break into the local network and start SSH brute forcing other accessible machines on the local network.
I agree that firewalls go a long way - but in this case the hacker did get past by, presumably, exploiting a vulnerability in Wordpress! I don’t really want to have to turn into a paranoid sys admin having to open and close ports on local machines all the time. I would rather start with a robust network configuration and then worry about each machine on the local network as best I can.
Possible Solution
I’m testing a setup using two routers and two separate DHCP fire-walled networks, based on the concept described here and tutorial here (though I’m not using VPN). See the attached image for a visual layout of the set up I’m testing.
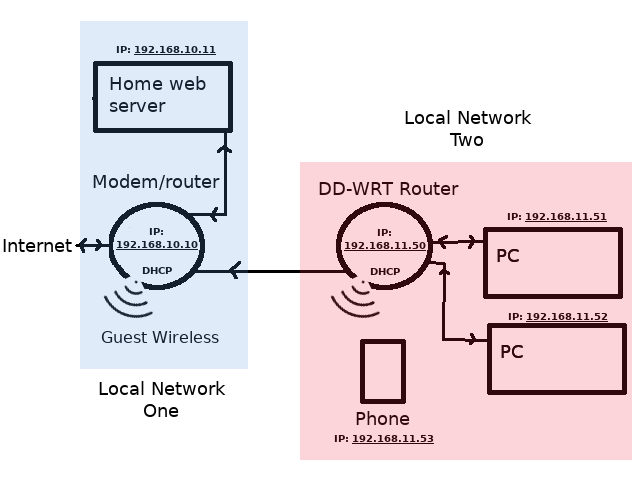
From information I have found it seems that network two (IP: 192.168.11.x - the “inner” network) can reach out to network one (IP: 192.168.10.x - the “outer” network) and to the internet. But the outer network can’t (easily) get past the second router’s firewall and into the inner network.
This works because data is passed back though the NAT to the originating address, but all other traffic is stopped by the firewall. So the local machines on the inner network can reach out and SSH into the server on the outer network, but the server can’t break through the inner firewall to reach the local machines on the inner network.
I have tested and I can SSH from within the inner network to the server on the outer network. But I don’t seem to be able to SSH from the server to a machine on the inner network, so it does seem to be the case that this set up gives me what I want.
I am new to all of this though, so I could be missing something obvious here.
Does my set up this make sense in the way I have described?