Connecting to a Third Party VPN with Freedombox via WireGuard
I got this working and wanted to share what I did with others. I’m not familiar with networking and it’s likely I’ve framed things poorly and might have used the wrong terms. I hope more experienced users will chime in to correct my mistakes. My knowledge is pretty thin.
I already had a Mullvad account. Mullvad allows you to have 5 “devices” defined and I used one of those slots for this setup. I have Freedombox version 24.24 running on a Raspberry Pi 4. Before beginning I installed the Wireguard app on Freedombox.
I followed these steps:
• Log in in to the Mulvad website and go to Mullvad’s Wireguard configuration page Log in | Mullvad VPN
• Click on “Generate key”
• Select an exit location. This is the mullvad server you want to use. For example I chose USA, McAllen TX, us-txc-wg-002
• Under Advanced settings you can see that
the Custom Port is 51820 which is what you want.
You can also configure content blocking if desired
• Click on the button to Download File and save it to your preferred location
(Downloads folder for example).
• This downloaded file gives you what you need to “Add a Connection
to Server” in the Freedombox Wireguard app.
• Let’s say your downloaded config file from Mullvad looks like this (keys and etc have been changed!):
[Interface]
# Device: Weird Panda
PrivateKey = Kxxxxxxxxxxxxxxxxxxxx=
Address = 10.71.99.190/32
DNS = 100.64.0.7
[Peer]
PublicKey = Wyyyyyyyyyyyyyyyyyyyyy=
AllowedIPs = 0.0.0.0/0
Endpoint = 79.127.222.207:51820
• Now, on your Freedombox, open the Wireguard app (previously installed)
• Click on “Add Connection to Server” near the bottom of the page and fill in the blanks according to the downloaded configuration file as pasted above. For example,
• - Endpoint of the server 79.127.222.207:51820
• - Public key of the server Wyyyyyyyyyyyyyyyyyyyyy=
• - Client IP address provided by server 10.71.99.190
• - Private key of this machine Kxxxxxxxxxxxxxxxxxxxx=
• - Pre-shared key: — leave this blank
• - Check the box for “Use this connection to send all outgoing traffic”
• - Click on “Add Connection”
Now, what remains is to set up the communication between the end-user machine (e.g. your laptop connected to your LAN) and Freedombox. On the Freedombox side, in the Wireguard app, you’ll “Add an Allowed Client” and on the end-user machine you’ll configure Wireguard accordingly. There is a Wireguard app on both Mac and Windows. I’m pretty sure on Linux, you’ll need to configure via the command line.
My test end-user machine is an old iMac. I got the Wireguard app from Apple’s app store. For your device, use the installation info from Installation - WireGuard. Now,
• Launch Wireguard on the end-user machine
• Create an empty tunnel
– This will create a private/public keypair
– Just leave this wireguard configuration window open while you set up the client information on Freedombox.
• In the Wireguard app on Freedombox, click on “Add Allowed Cient”
• Enter the public key you’ve got from from the end-user wireguard app.
• Click “Add Client” on the Freedombox
The resulting client information on Freedombox gives you what you need to fill in the empty tunnel on the end-user wireguard app. To see all the client information at once, click on the link for the connection you just created. You’ll see the IP address, the endpoint, and the freedombox server public key.
Let’s say the client information generated by Freedombox looks like this:
Client public key: 3uzzzzzzzzzzzzzzzzzzzzzzzz=
IP address to use for client: 10.80.0.9
Pre-shared key: None
Server endpoints: freedombox.local:51820
Server public key: njnnnnnnnnnnnnnnnnnnnnnnn=
In addition, you’ll also use the DNS address that was given in the Mullvad configuration file “DNS = 100.64.0.7”
And when you created an empty tunnel on the end-user machine, Wireguard created the corresponding private key, for example
wNppppppppppppppppppppppppppppp=
You’ll see that, pre-populated, in Wireguard on the end-user machine. Below, I used the endpoint freedombox.local:51820 but you can also use the dotted quad IP address of your freedombox e.g. 192.168.0.73:51820 or whatever it may be on your LAN.
Here’s the correctly formatted infomation from above pasted into the end-user Wireguard app.
[Interface]
PrivateKey = wNppppppppppppppppppppppppppppp=
ListenPort = 51820
Address = 10.80.0.9
DNS = 100.64.0.7
[Peer]
PublicKey = njnnnnnnnnnnnnnnnnnnnnnnn=
AllowedIPs = 0.0.0.0/0
Endpoint = freedombox.local:51820
And then check the box for “Exclude Private IPs”
• Click Save for the end-user Wireguard tunnel configuration
• ‘Activate’ the end-user Wireguard tunnel
Ideally you should now have a working tunnel to your Freedombox and from the Freedombox to Mullvad. To test, go to https://mullvad.net and see if it says that you’re using Mullvad in the top banner.
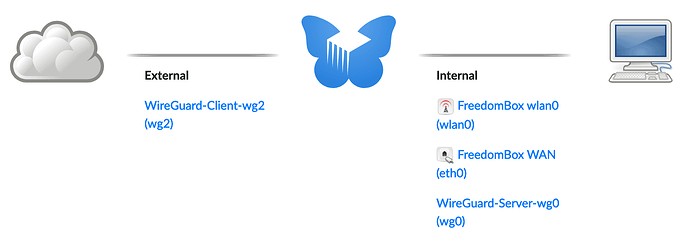
It’s fairly awkward for me to write this clearly. There are so many
keys, computers, and interfaces. Note that the Freedombox Wireguard app creates two interfaces. In this scenario, there is an internal interface which communicates inside the LAN to your end-user machine. There is also an external interface which is forwarding all traffic to the Mullvad server over the internet. Each of these interfaces supports a Wireguard Peer with its own Public Key. So, yes there are two public keys needed to complete this setup.
In short, the Freedombox Wireguard app creates an internal network interface that acts as a wireguard server inside your LAN for a client on your end-user machine. The external Freedombox network interface is acting as a client to the Mullvad server on the internet. I think that’s right.